1、实战-Cerbot结合阿里云dns插件实现自动续期-20250305(测试成功)(推荐)
实战-Cerbot结合阿里云dns插件实现自动续期-20250305(测试成功)(推荐)
目录
[toc]
版权
参考《Hyde》大佬的《Certbot实现 HTTPS 免费证书(Let‘s Encrypt)自动续期》文章,十分感谢作者的手把手文档💖💖。
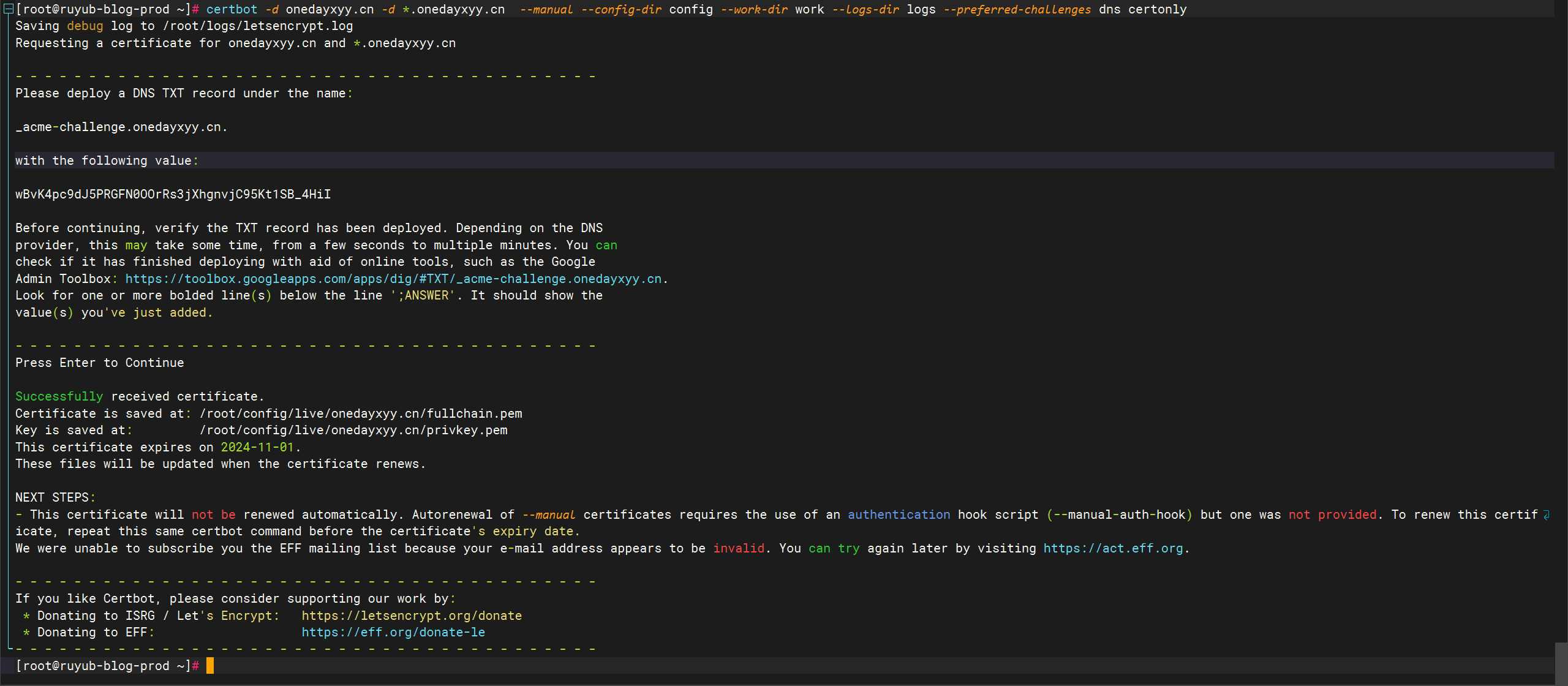
通过 dns 通配符去实现自动续期这里推荐 @justjavac 大佬写的:https:tarxzvfaliyun-cli-linux-latest-amd64.tgzsudocpaliyun/usr/local/binrm-faliyun
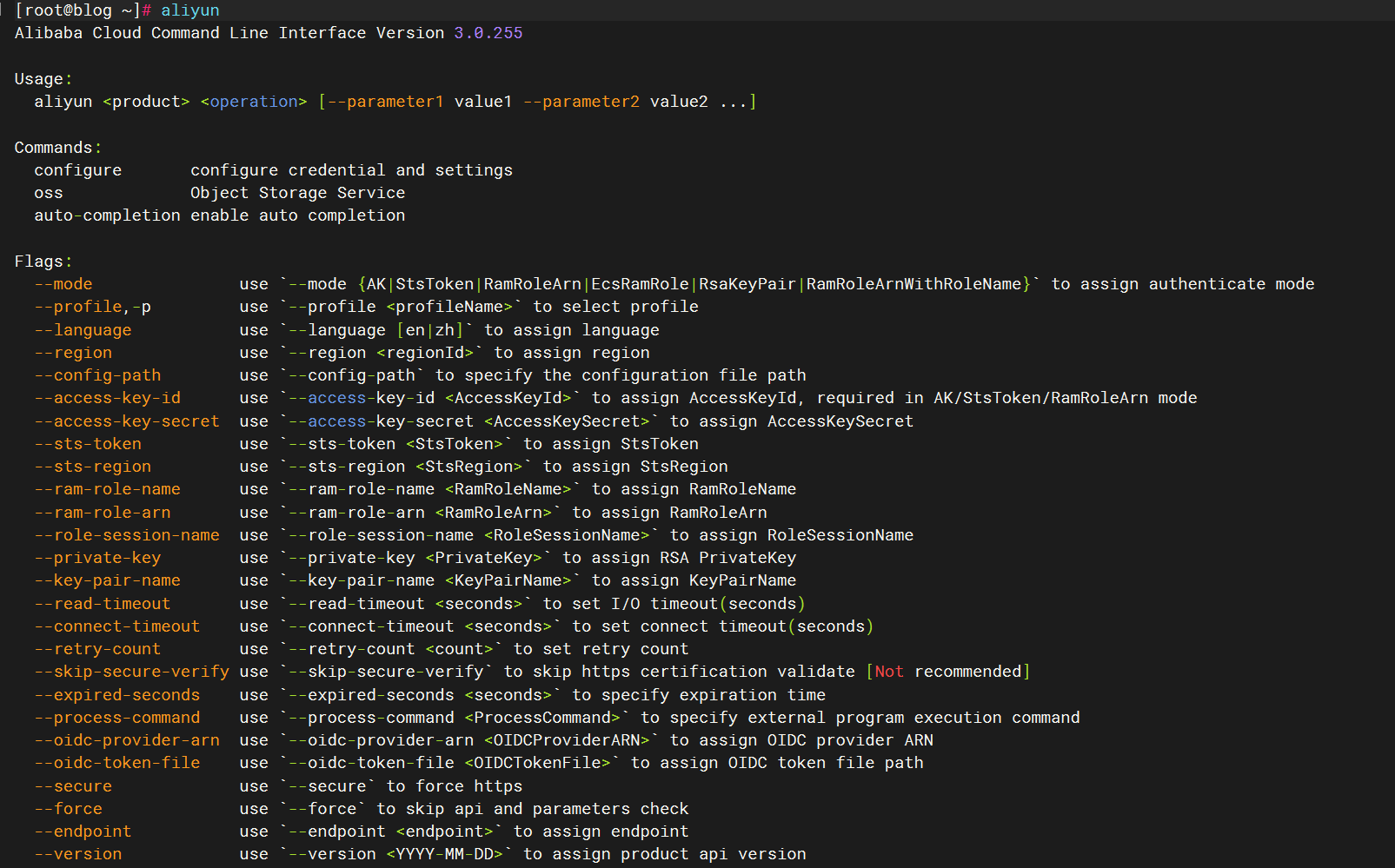
验证 aliyun cli 工具是否成功:
打开终端,输入 aliyun命令并回车。如果安装成功,会显示阿里云 CLI 的帮助信息,包含可用的命令和选项
示例输出如下:
🍊 (2)安装 certbot-dns-aliyun 插件
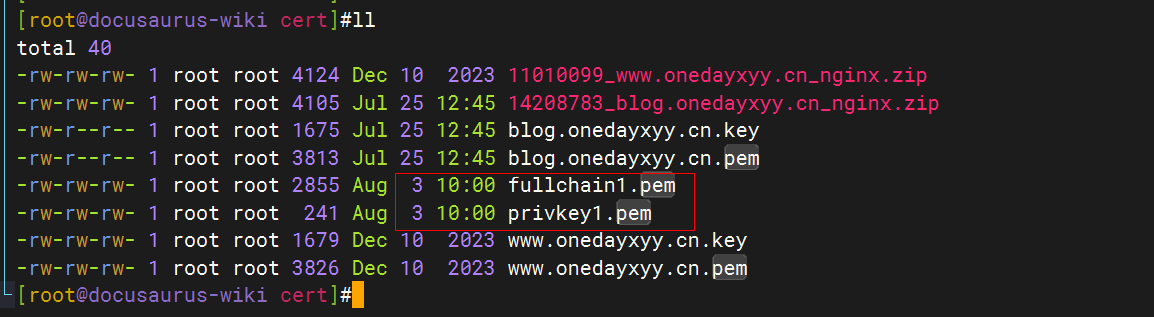
#下载、部署并配置一个名为 alidns.sh 的脚本wgethttps:sudocpalidns.sh/usr/local/binsudochmod+x/usr/local/bin/alidns.shsudoln-s/usr/local/bin/alidns.sh/usr/local/bin/alidns如果下载失败手动前往 github 下载:https:#这里秘钥我加过密的哦
按照提示输入你的阿里云访问密钥(AccessKey ID 和 AccessKey Secret)、默认的地域 ID 等信息,配置完成后就可以使用阿里云 CLI 工具来管理你的阿里云资源了。
如何获取阿里云访问密钥(AccessKey ID 和 AccessKey Secret)请参考官方文档:https:Profile|Credential|Valid|Region|Language---------|------------------|-------|----------------|--------default||Invalid||enAkProfile*|AK:***jAc|Valid|oss-cn-shanghai|en#目前存在两个配置文件,分别是 default 和 AkProfile。其中 AkProfile 后面带有 *号,这表明当前使用的默认配置文件是 AkProfile。